SECTION |
TITLE |
INSTRUCTIONS |
|
|
|
|
1 |
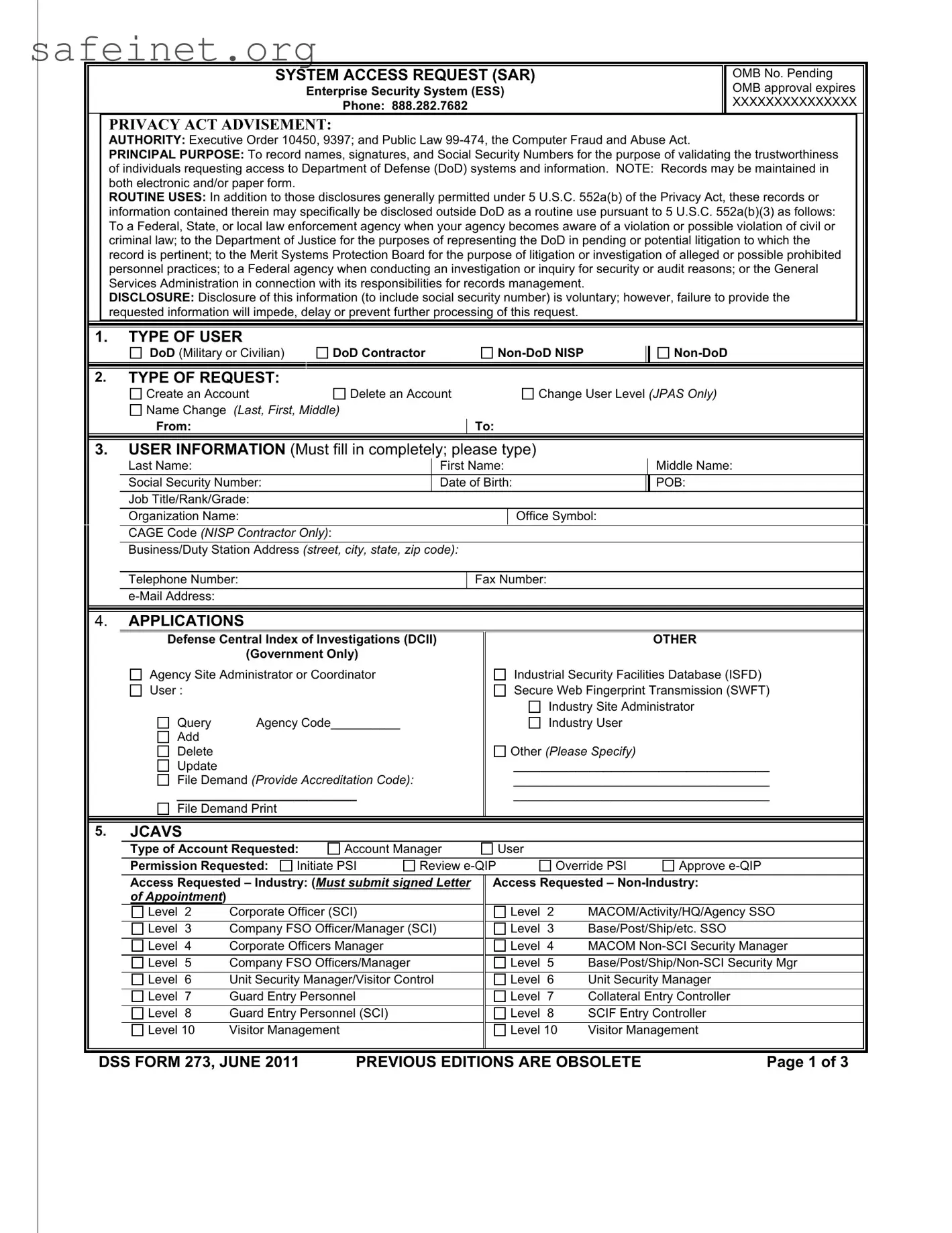
TYPE OF USER |
Check the appropriate box for DoD (e.g., Military Branches, DoD Agencies), DoD |
|
|
Contractor Companies, Non-DoD NISP Partners and Non-DoD affiliated. |
|
|
|
|
|
2 |
TYPE OF REQUEST |
Check the appropriate box indicating purpose for the SAR. |
|
|
|
|
3 |
USER INFORMATION |
Must completely fill in. If no middle name, enter NMN. Ensure e-mail address is accurate; |
|
|
account access credentials are transmitted via e-mail. |
|
|
|
|
|
4 |
APPLICATIONS |
Check the application(s) and function(s) the user requires. |
|
|
|
|
|
5 |
JCAVS |
Check appropriate boxes. See definitions below. |
|
|
|
NOTE: The appointment letter must be drafted on company letterhead, must name the |
|
|
Primary Account Manager and must be signed by a corporate officer (KMP). The same |
|
|
KMP must sign both the SAR (nominating official) and the letter. |
|
|
|
|
5 |
ACCOUNT MANAGER |
Account Managers will provide account maintenance on all user accounts created within |
|
|
their company. Responsibilities include, but are not limited to, locking/unlocking accounts, |
|
|
resetting passwords, logging off users, deleting accounts when no longer needed and |
|
|
maintaining their Security Management Offices (SMO). Account managers will create any |
|
|
additional accounts that are required. |
|
|
|
|
5 |
USER |
Depending on the level of access, users may verify clearances, update accesses, process |
|
|
visit notifications, and handle all other functions within JCAVS. |
|
|
|
|
|
5 |
ACCESS REQUESTED – |
Check appropriate block, using the following guidance: |
|
|
INDUSTRY |
Level 2: SCI security personnel at Corporate level, with read and write access. |
|
|
Level 3: SCI security personnel at echelons subordinate to Level 2 at a particular |
|
|
geographic location, with read and write access. |
|
|
|
Level 4: Non-SCI security personnel at Corporate level, with read and write access. |
|
|
Level 5: Non-SCI security personnel immediately subordinate to Level 4, with read and |
|
|
write access. |
|
|
|
Level 6: Non-SCI security personnel immediately subordinate to Level 5, with read and |
|
|
write access. |
|
|
|
Level 7: Non-SCI security personnel who accomplish entry control (i.e., access to |
|
|
installations, buildings, etc.), with read-only access. |
|
|
|
Level 8: SCI security personnel who accomplish entry control, with read-only access. |
|
|
Level 10: Non-SCI security personnel who accomplish visitor management, with read-only |
|
|
access. |
|
|
|
|
|
5 |
ACCESS REQUESTED – |
Self-explanatory; check appropriate block. |
|
|
DoD (NON-INDUSTRY) |
|
|
|
|
|
N/A |
TOP OF PAGE 2 |
Ensure User’s last name and first initial are entered at the top of the page in the space |
|
|
provided. |
|
|
|
|
6 |
JAMS USER ROLES |
Provide information and check appropriate boxes for user functions, access, and |
|
|
permissions. JAMS is only authorized for DoD CAFs. |
|
|
|
|
7 |
NOMINATING OFFICIAL’S |
The Nominating Official is the individual who is authorizing that the User should have the |
|
CERTIFICATION |
requested accesses. The Nominating Official may be a Corporate Officer (KMP), Facility |
|
|
Security Officer, Security Manager, Information Systems Security Officer, Agency |
|
|
Administrator, etc. For JCAVS Industry Primary Account Managers, the SAR must be |
|
|
signed by the same KMP that signed the Appointment Letter. The Nominating |
|
|
Official CANNOT be the same as the User. Exceptions include the company President, |
|
|
for JCAVS, and the FSO, for ISFD. NOTE: SARs submitted without the Nominating |
|
|
Official’s signature included will not be processed. |
|
|
|
|
|
8 |
USER’S CERTIFICATION |
User must sign, acknowledging DoD/system policy. |
|
|
|
|
9 |
VALIDATING OFFICIAL’S |
The DoD Security Services Center (for industry only) or the Security Manager must verify |
|
VERIFICATION |
and indicate the following information on the following lines prior to signing: Clearance |
|
|
Level; Clearance Granted Date; Clearance Issued By; Type of Investigation; Date |
|
|
Investigation Completed; and Investigation Conducted By. For non-DoD government |
|
|
agency requests, the Chief of Security or designee must complete this section. |
|
|
|
|
10 |
ADDITIONAL SAR |
Provided to facilitate successful processing of the SAR. |
|
|
DIRECTIVES |
|
|
|
|
|
|
DSS FORM 273 (INSTRUCTIONS), JUNE 2011 |
Page 3 of 3 |